What is Cloudanix?
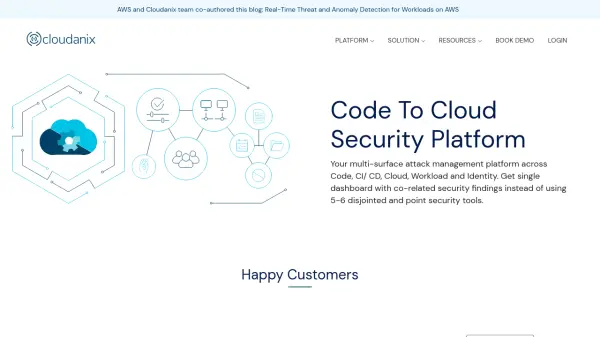
Cloudanix provides a comprehensive security solution designed to manage multi-surface attacks across various environments including code repositories, CI/CD pipelines, cloud infrastructure, workloads, and identity management systems. It aims to replace multiple point security tools by offering a single dashboard with correlated security findings, facilitating easier prioritization and remediation. The platform focuses on securing development processes early (Shift Left) by identifying vulnerabilities like secret exposures, SAST findings, and open-source issues before they reach production, providing context and remediation playbooks for developers.
The platform extends its capabilities to cloud security posture management (CSPM), identifying over 1000 misconfigurations mapped to compliance standards such as HITRUST, SOC2, HIPAA, and CIS, complete with customizable policies and remediation guidance. It also includes Cloud Workload Protection Platform (CWPP) features for container security, covering image scanning, configuration checks, and runtime threat detection across various Kubernetes environments. Additionally, Cloudanix addresses identity security through Cloud Infrastructure Entitlement Management (CIEM), offering Just-In-Time (JIT) access and least privilege management to mitigate risks associated with over-provisioned permissions.
Features
- Code Security: Integrates SAST, SCA, secret scanning, and IaC security into development workflows.
- Cloud Security Posture Management (CSPM): Identifies and helps remediate cloud misconfigurations against various compliance standards.
- Cloud Workload Protection Platform (CWPP): Secures host and container workloads, including image scanning and runtime threat detection.
- Cloud Infrastructure Entitlement Management (CIEM): Manages cloud identities and permissions, offering Just-In-Time (JIT) access.
- 1-Click Remediation: Provides built-in remediation playbooks for identified security issues.
- Threat & Anomaly Detection: Real-time detection of security threats and anomalies.
- Attack Path Analysis: Visualizes potential attack vectors from outside-in perspective.
- Compliance Monitoring: Helps manage and report on compliance standards like SOC2, HIPAA, CIS, etc.
- Query Builder: Allows custom queries on security data.
- Multi-Cloud Support: Integrates with AWS, Azure, GCP, Digital Ocean, Oracle Cloud.
Use Cases
- Implementing DevSecOps practices by integrating security into the development lifecycle.
- Achieving and maintaining compliance with standards like SOC2, HIPAA, PCI DSS, etc.
- Consolidating multiple security tools into a single platform.
- Securing cloud-native applications and infrastructure (Kubernetes, containers).
- Managing cloud identity risks and implementing least privilege access.
- Detecting and responding to cloud security threats in real-time.
- Improving cloud asset visibility and security posture management.
Related Queries
Helpful for people in the following professions
Featured Tools
Join Our Newsletter
Stay updated with the latest AI tools, news, and offers by subscribing to our weekly newsletter.