What is Stitchflow?
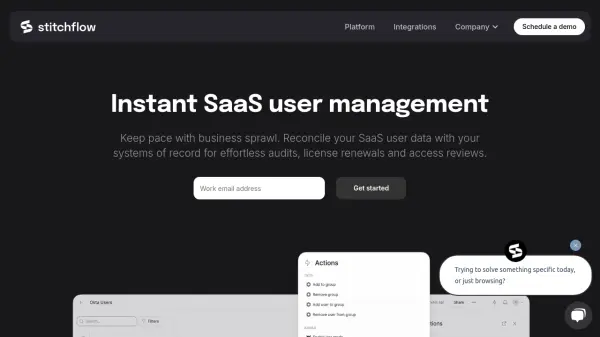
Stitchflow is an AI-powered platform designed to address the complexities of modern IT environments by providing comprehensive SaaS user management. It automatically maps access policies, exceptions, and variables across an organization's entire application landscape, including non-SCIM applications. This detailed mapping allows the platform to conduct continuous access reviews, pinpointing specific accounts requiring attention without generating unnecessary alerts, thereby streamlining IT workflows.
The platform integrates data from various sources, including cloud-native applications and CSV imports from legacy systems, offering a unified view of the cloud IT infrastructure. Stitchflow helps IT teams identify and remediate critical user access and license gaps, such as ex-employees retaining access, users not synced with the Identity Provider (IDP), and license wastage from inactive or underutilized accounts. It adapts to organizational changes like growth, reorganizations, and M&A, ensuring consistent visibility and control over SaaS usage and access security.
Features
- AI-Powered Access Reviews: Continuously reviews access across all applications, pinpointing accounts needing attention.
- Comprehensive Mapping: Maps all access policies, exceptions, and variables (employee, contractor, role, non-SCIM app).
- Data Integration: Stitches data from diverse sources, including cloud apps (50+ integrations) and CSV imports for legacy systems.
- Precise Reporting: Generates spreadsheet-like reports for license management, offboarding completeness, and compliance.
- License Optimization: Identifies hidden license waste from ex-employees, contractors, and underutilized licenses.
- Gap Identification: Catches access misses like ex-employees with tool access and users not present in the IDP.
- Adaptive Platform: Automatically adapts to organizational changes (growth, M&A, reorganizations).
Use Cases
- Conducting comprehensive SaaS access reviews.
- Managing and optimizing software license renewals.
- Ensuring complete user offboarding across all applications.
- Maintaining compliance and security standards for user access.
- Auditing user access across SCIM and non-SCIM applications.
- Reducing manual effort in IT audits and data reconciliation.
- Gaining unified visibility into cloud IT tools and user data.
Related Queries
Helpful for people in the following professions
Stitchflow Uptime Monitor
Average Uptime
99.86%
Average Response Time
112.57 ms
Featured Tools
Join Our Newsletter
Stay updated with the latest AI tools, news, and offers by subscribing to our weekly newsletter.