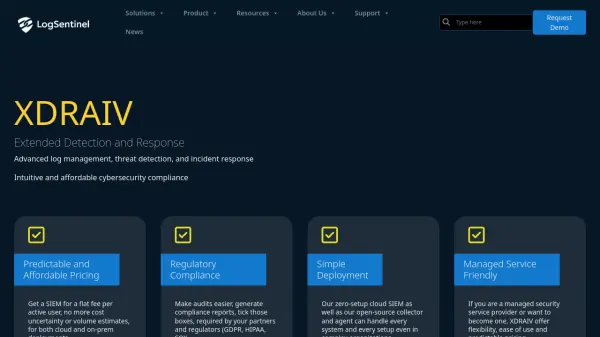
What is LogSentinel XDRAIV?
The platform integrates with external threat intelligence feeds to enhance detection accuracy against emerging threats, known malware, vulnerabilities, and malicious actors. Key functionalities include continuous file integrity monitoring to protect data integrity and detect unauthorized changes, alongside user behavior analysis to identify anomalies and potential internal threats. LogSentinel XDRAIV provides flexible deployment options, including a zero-setup cloud SIEM and an open-source collector, suitable for various organizational sizes and complexities, including managed security service providers (MSSPs).
Features
- Log Management: Centralized log collection, normalization, enrichment, and analysis.
- Threat Detection: Advanced correlation and integration with external threat intelligence feeds.
- Incident Response: Tools to manage and respond to security incidents.
- Regulatory Compliance: Features to meet GDPR, HIPAA, SOX, PCI-DSS, PSD2 standards, including reporting.
- File Integrity Monitoring: Continuous monitoring and alerting on file modifications.
- User Behavior Analysis: Identifies anomalies and potential threats based on user activities.
- Security Assessment: Comprehensive assessments to identify vulnerabilities and compliance risks.
- Cloud & On-Prem Deployment: Flexible deployment options including cloud SIEM and on-premise installation.
Use Cases
- Centralizing log data from various systems for analysis.
- Detecting and responding to cybersecurity threats in real-time.
- Meeting regulatory compliance requirements (GDPR, HIPAA, PCI-DSS, etc.).
- Monitoring file integrity to prevent unauthorized data changes.
- Analyzing user behavior to identify insider threats or compromised accounts.
- Performing security assessments to identify vulnerabilities.
- Providing managed security services (MSSP).
- Securing cloud-based infrastructure.
- Monitoring on-premise security environments.
Related Queries
Helpful for people in the following professions
LogSentinel XDRAIV Uptime Monitor
Average Uptime
98.99%
Average Response Time
1506.14 ms
Featured Tools
Join Our Newsletter
Stay updated with the latest AI tools, news, and offers by subscribing to our weekly newsletter.