What is LeakSignal?
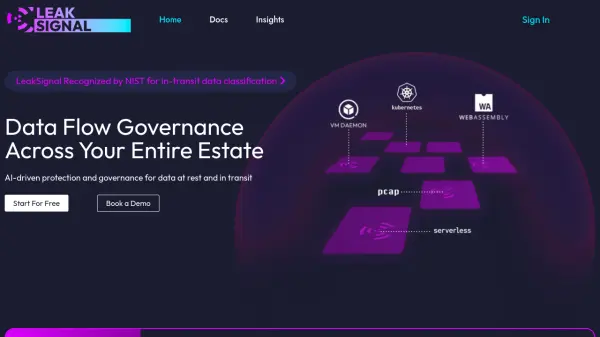
LeakSignal offers comprehensive data flow governance across your entire estate. The platform provides AI-driven protection and governance for sensitive data, both at rest and in transit.
It ensures security and compliance through real-time data classification, comprehensive data flow analysis, enhanced regulatory compliance, and complete GenAI governance. LeakSignal seamlessly integrates with existing infrastructure, offering policy-based enforcement of sensitive data handling. It is recognized by NIST for in-transit data classification.
Features
- Real-Time Data Classification: Classify sensitive data in-transit, allowing for policy-based enforcement and governance of data flows.
- Comprehensive Data Flow Analysis: Detailed insights into how data is accessed, used, and transmitted across your infrastructure, enabling better decision-making and incident response.
- Enhanced Regulatory Compliance: Continuous monitoring and control over data flows, ensuring that all data access and transmission activities are logged and audited.
- Complete GenAI Governance: Govern data usage in generative AI models, ensuring that sensitive data flows are monitored and compliance standards are upheld.
- Endpoint Governance: Complete governance and protection for endpoints.
- GenAI Data Flow Protection: Deploy and protect GenAI workloads with data flow classification for LLM inputs and outputs.
- Sensitive Data Flow Observation: Observe and protect all sensitive data flows.
- Log Pipeline Leakage Prevention: Observe and redact sensitive data before it is sent into logs and storage systems.
- 3rd Party Data Audit and Protection: Observe sensitive data being sent to 3rd parties from production workloads in cloud and on-prem environments.
Use Cases
- Protecting intellectual property and sensitive data when employees access third-party GenAI.
- Deploying and protecting GenAI workloads.
- Mapping data flows across cloud environments.
- Inventorying and protecting APIs.
- Detecting data leakage, exploits, and PII exposure in live traffic.
- Preventing sensitive data leakage in log pipelines.
- Auditing and protecting data sent to third parties.
Related Queries
Helpful for people in the following professions
LeakSignal Uptime Monitor
Average Uptime
99.45%
Average Response Time
1302.83 ms
Featured Tools
Join Our Newsletter
Stay updated with the latest AI tools, news, and offers by subscribing to our weekly newsletter.